Security/Reviews/B2G/NetworkAlerts
/!\ WORK IN PROGRESS /!\
Overview
Firefox Accounts Review Details
- Scope: Timeboxed review of Network Alerts for Firefox OS
- Review Date: 2014-09-12
- Review Lead: Christiane Ruetten, cr@mozilla.com
Documentation
Context
Network Alerts is an implementation of a subset of the ETSI Pulic Warning System (PWS) for Firefox OS 2.1. The PWS standard uses a mobile network's Cell Broadcast Service (CBS) to alert mobile phone users, located in a certain area, to civil or national threats or emergencies, for example earthquakes, tornadoes, and the US-specific AMBER Alerts in case of child abduction.
PWS supports multiple message identifiers which map to the various international alert providers and message types, of which Firefox OS's Network Alerts supports only a subset. Some regulations require mobile endpoints to support relevant national PWS channels.
Upon reception of a CBS message, a mobile device is to determine the alert type, and in case of a PWS message, to display the alert's content in a popup fashion that does not require user interaction.
Scope
Network Alerts consists of a Gaia component handling user interaction and modifications to the Gonk code that interfaces the RIL layer — where cell broadcasts enter the system — with the Gaia world.
The following components were reviewed:
- Network Alerts Gaia app
- PWS-related code in System notification handling
- Changes to System Messages permission handling
- PWS-related changes in the Gonk RIL helper
The following components were not reviewed:
- PWS-handling inside the RIL due to lack of code
- Settings changes
- Tests
Relevant Source Code
Gaia
- https://mxr.mozilla.org/gaia/source/apps/network-alerts/
- https://mxr.mozilla.org/gaia/source/apps/system/js/notifications.js
- https://mxr.mozilla.org/gaia/source/apps/system/test/unit/notifications_test.js
Gonk
- https://mxr.mozilla.org/mozilla-central/source/dom/system/gonk/RadioInterfaceLayer.js
- https://mxr.mozilla.org/mozilla-central/source/dom/system/gonk/ril_worker.js
- https://mxr.mozilla.org/mozilla-central/source/dom/system/gonk/RILContentHelper.js
Other
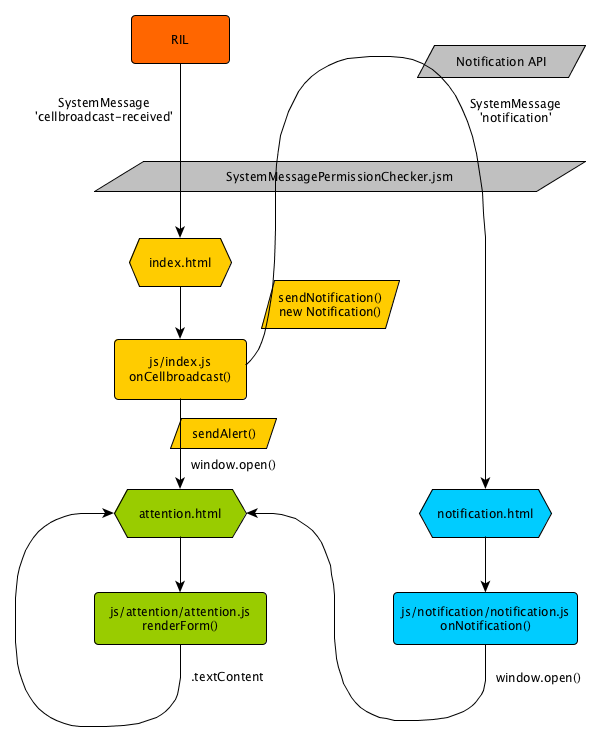
Architecture
RIL is the single source of data for alert messages. It triggers 'cellbroadcast-received' system messages which contain type and body of the broadcast received. Network Alerts registers a onCellbroadcast() event listener, filters for relevant message types and then displays a popup attention message containing only the cellbroadcast message body as external variable content.
In parallel, it opens a new Notification() in the notification tray which generates a 'notification' system message when selected when selected. 'notification' messages are handled by a listener which also opens the attention message.
attention.html and notification.html are called with windows.open() calls. Message body and title (which is static) are securely encoded using .encodeURIComponent().
Data Flow
Data in Network Alerts originates solely from the RIL layer via 'cellbroadcast-received' system messages. The data sinks are attention.html, which receives the broadcast message body through a .textContent operation, and a Notification object which is deemed safe handling untrusted data.
Permission Model
The app manifest defines a certified app running in the system role. Four permissions are requested: attention, desktop-notification, cellbroadcast and readonly settings access. The manifest also registers system message handlers for cellbroadcast-received and notification.
1 {
2 "name": "Network Alerts",
3 "description": "Handling network alerts (like CMAS)",
4 "type": "certified",
5 "launch_path": "/index.html",
6 "role": "system",
7 "developer": {
8 "name": "The Gaia Team",
9 "url": "https://github.com/mozilla-b2g/gaia"
10 },
11 "icons": {
12 "30": "/style/icons/icon-30.png",
13 "45": "/style/icons/icon-45.png",
14 "60": "/style/icons/icon-60.png",
15 "68": "/style/icons/icon-68.png"
16 },
17 "permissions": {
18 "attention":{},
19 "desktop-notification":{},
20 "cellbroadcast":{},
21 "settings":{ "access": "readonly" }
22 },
23 "default_locale": "en-US",
24 "orientation": "default",
25 "messages": [
26 { "notification": "/notification.html" },
27 { "cellbroadcast-received": "/index.html"}
28 ]
29 }
Risks and Mitigations
Threat Model overview
| Threat | Description | Mitigation |
| Base Station compromise | An attacker can set up a compromised base station and send arbitrary cell broadcast messages to connected devices. | Proper input handling, input validation, de-duplication, rate-limiting |
| Malicious local app | Unauthorized apps could trigger arbitrary alert events and flood the user with alert messages. | Permission model, event filtering |
Base Station compromise
Malicious local app
generating and receiving 'cellbroadcast-received' events is properly limited to apps with 'cellbroadcast' permission.
in future FxOS versions that are planned to enable IPC via window.open()
Actions & Recommendations
- Implement alert de-duplication for re-broadcasted PWS events.
- Work out architectural change that prevents malicious local apps from sending GET requests to attention.html and notification.html.
- Message authentication via secret token?
- Different calling mechanism?
Bugzilla references
- Bug 1067295 - Network Alerts security review for the FxOS 2.1 release
- Bug 1026685 - (cmas-application) CMAS Alert channel support
- Bug 1055994 - Fire system message for cell broadcast