IAM/Frequently asked questions
Mozilla IAM FAQ (Frequently Asked Questions)
Q: What is Mozilla IAM?
Mozilla IAM stands for Mozilla's Identity and Access Management. It's the system that Mozilla manages logins to various web properties and systems.
Usually, you'd use Mozilla IAM as Mozilla Staff, or as a contributor with access to the tools and resources Mozilla uses day to day. An example of that would be our Discourse instance: http://discourse.mozilla.org/
Mozilla IAM is not Firefox Accounts, Persona or part of any Mozilla Product.
Q: How do I login with Mozilla IAM?
Mozilla IAM supports various login methods, such as "LDAP" (Staff logins), Firefox Accounts login, GitHub social login, Google social login and email login (which we call "passwordless"). Certain methods support and enforce the use of two-factor authentication (2FA) and may grant access to more sensitive services.
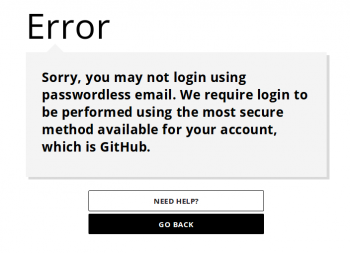
Q: Why is my login failing with an error message telling me to use "Firefox Accounts/GitHub/Google/LDAP/etc" instead?
If your login (your primary email address used by Mozilla IAM) matches an existing account which provides higher security, we require that you use the most secure method available to login.
Example: LDAP uses two-factor authentication to verify a user's identity and is safer than using email login ("passwordless").
Q: Why do you support email login ("passwordless") if it's less safe than other methods?
Sometimes all you want to do is post a comment on a public forum. For that, we often need to provide a valid identity, but we also want to make it as easy as possible for you to contribute. Email login ("passwordless") is our current solution for this use case. Some applications we provide may not provide this login method, for example when the application requires more secure methods.
Q: I would like access to specific groups, such as the NDA group, but it requires me to use a different login method, why?
We only allow login, or authentication methods that can verifiably require two-factor authentication (2FA) in order to join any group that may grant you access to data that is not public, such as what we call STAFF CONFIDENTIAL data. At the time of writing, only LDAP, Google accounts that use our LDAP backend (i.e. not '@gmail.com' accounts), Firefox accounts and GitHub accounts support this functionality.
Example: you could get a GitHub account with two-factor authentication enabled. Here's some documentation on how to do this: https://help.github.com/articles/about-two-factor-authentication/. Firefox Accounts also supports two-factor-authentication: https://blog.mozilla.org/services/2018/05/22/two-step-authentication-in-firefox-accounts/.
If more authentication methods add support for this in the future and seem to be otherwise safe, we'll gladly allow them as well.
Q: I used to use email login ("passwordless") to access STAFF CONFIDENTIAL data with my NDA'd account, but I lost access
We no longer allow email logins to access non-PUBLIC data (see previous FAQ item as well). In order to regain access, please use a login method that supports two-factor authentication (2FA) such as GitHub. Here's some documentation on how to do this: https://help.github.com/articles/about-two-factor-authentication/
Q: Where is the source code, documentation, etc. for all Mozilla IAM Projects?
Glad you asked! it's all here: https://github.com/mozilla-iam/mozilla-iam/
Q: I found a bug, vulnerability, issue, etc. Where do I report it?
Please report all public bugs and issues here: https://github.com/mozilla-iam/mozilla-iam/issues For security vulnerabilities, please see https://www.mozilla.org/en-US/security/bug-bounty/web-eligible-sites/ or email us at security@mozilla.org Thanks for your help!
Q: My question is not listed here, where can I reach out?
You can find a link to our public discussion board here: https://github.com/mozilla-iam/mozilla-iam/#discussion
Q: How do I create a Non-Staff Mozillians Account that will work for SSO
To be able to be added to access groups in Mozillians, your Mozillians account must be associated with a supported login identity.
A Mozillians account must be associated with one of the following login identities with multi-factor authentication enabled to be added to access groups.
Mozilla LDAP (required during set-up)
- Firefox Accounts
- GitHub
1. If you don't already have an account with a supported login identity, create one by following the instructions from the provider 2. Enable 2FA/MFA authentication
If you set up 2FA on GitHub then you must select GitHub when creating your Mozillians account. If you set up 2FA on you Firefox account then you must select Firefox when creating your Mozillians account.
If your email account is provided by Google we recommend setting up 2FA in your Google account settings. If you don't want to set up 2FA on your Google account itself you can still use this address to create a GitHub or Firefox Account with 2FA enabled.
Sign-up For Mozillians
To keep things simple, it is very important that when creating your Mozillians account you choose the login method that has 2FA/MFA associated with it. If you set up 2FA/MFA on GitHub or Firefox Accounts do not select Google when logging in.
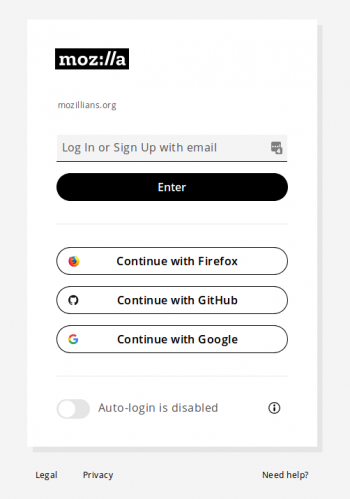
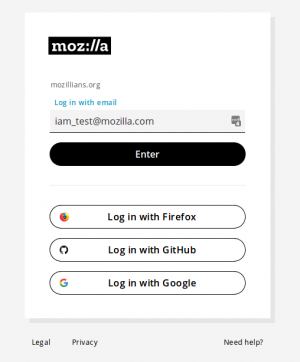
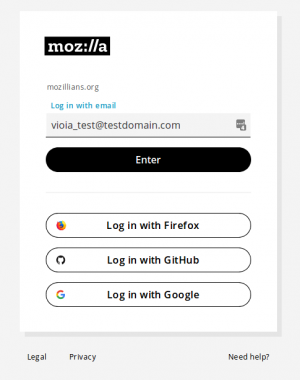
Go to mozillians.org Click on Log in / Sign up
Select the identity type that has 2FA/MFA enabled. DO NOT type your email into the "Log In or Sign Up with email" box. Remember, if you set up 2FA on your GitHub account then you must select GitHub when creating your Mozillians account.
Fill out the required fields and click the button to Complete Registration
Note: content blockers, including Firefox's built in settings, may hide the captcha. Ensure all the required fields are visible to be able to complete registration.
Q: How can I set up two-factor authentication (2FA) for my github account, using an app on my phone (Android/iOS/Blackberry)?
Two-factor authentication can be configured by using a Time-based One-Time Password (TOTP) application, which automatically generates an authentication code that changes after a certain period of time. See configuration steps below.
1. Download one of these apps:
- For Android, iOS, and Blackberry: Google Authenticator
- For Android and iOS: Duo Mobile
- For Windows Phone: Authenticator
2. In the upper-right corner of any GitHub page, click your profile photo, then click Settings.
3. In the user settings sidebar, click Security.
4. Under Two-factor authentication, click Set up two-factor authentication.
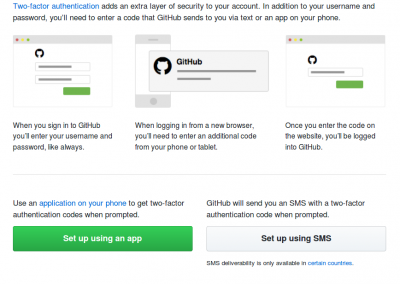
5. On the Two-factor authentication page, click Set up using an app.
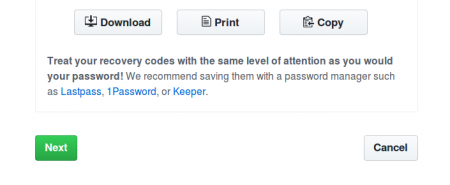
6. To enable two-factor authentication you must save your two-factor recovery codes in a safe place, such as a password manager, by clicking Download, Print, or Copy. Your recovery codes will help get you back into your account if you've lost access. After saving your codes, click Next.
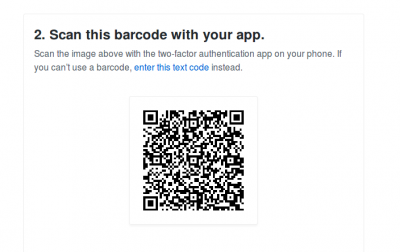
7. Scan the QR code with your mobile device's app. After scanning, the app will display a six-digit code that you can enter on GitHub.
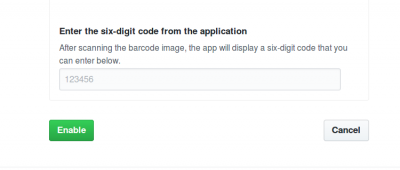
8. The TOTP mobile application will save your GitHub account and generate a new authentication code every few seconds. On GitHub, on the 2FA page, type the code and click Next.
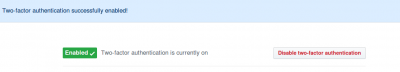
9. Verify that a success message is shown
10. After 2FA has been enabled and you've saved your recovery codes, we recommend you sign out and back in to your account. In case of problems, such as a forgotten password or typo in your email address, you can use recovery codes to access your account and correct the problem.
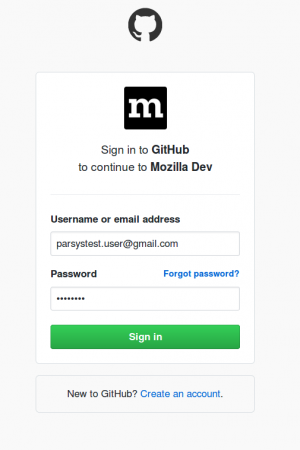
Q: I have an email address for my mozillians account different than the email I set as primary in my github account. How can I upgrade my mozillians account from passwordless to github?
1. In the following steps we assume you have 2FA set for your github account. If not, see the steps from here
2. Login to mozillians with your email.
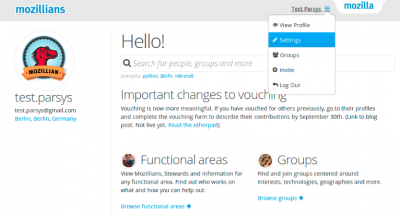
3. Navigate to profile settings page.
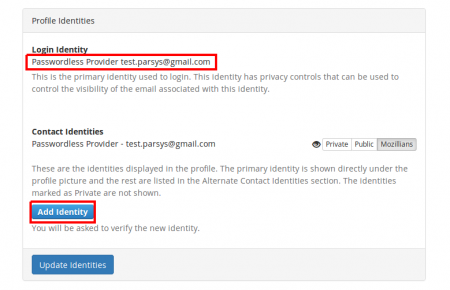
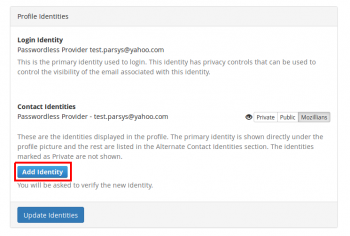
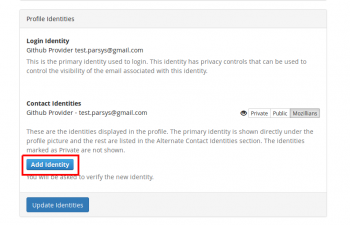
4. Scroll down to “Profile Identities” section and click “Add Identity” button.
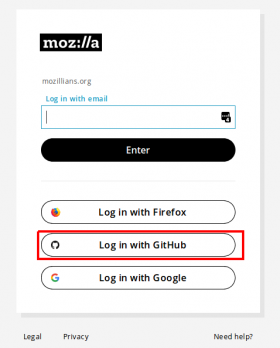
5. Select “Log in with Github” option in next page.
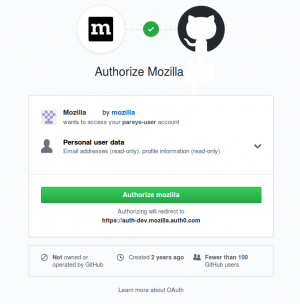
6. Click Authorize mozilla. If you’re logged in to github in the same browser, you can skip the next 2 steps.
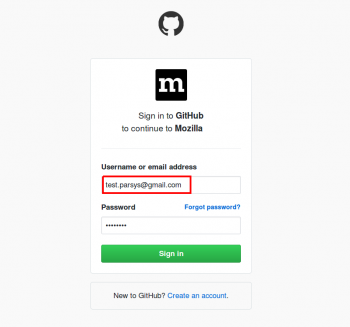
7. Enter github credentials and click “Sign In” button.
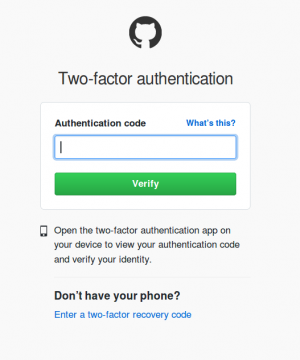
8. Enter the two-factor authentication generated by the app or received on your phone via text message.
9. Verify that success message is displayed, after adding the new github identity.
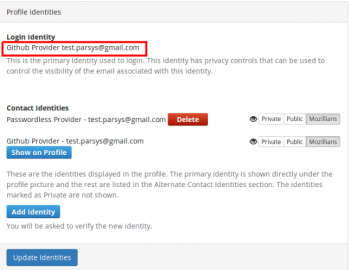
10. Scroll down to “Profile Identities” section and verify that your github account is set as your login identity. That means this is the account you should use from now on to login to mozillians.
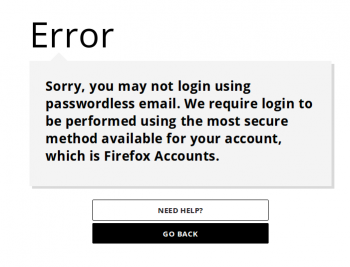
11. Trying to login with email to mozillians will return an error page, asking to login with github.
Q: The email address I use to login to my mozillians account matches the primary email of my github account. How can I upgrade my mozillians account from passwordless to github?
1. In the following steps we assume you have 2FA set for your github account. If not, see the steps from here.
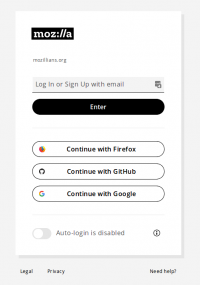
2. Navigate to mozillians page and click Log In/Sign Up button.
3. Select “Continue with Github” method from mozillians login page.
4. Enter Github credentials.
5. Enter 2fa code from your application.
6. Navigate to Settings -> Profile Identities section, and verify that Github is set as your login identity. That means this is the only account you can use from now on to login to mozillians.
7. Trying to login with email to mozillians will return an error page, asking to login with github.
Q: The email address I use to login to my Mozillians account matches the primary email of my Firefox Accounts account. How can I upgrade my Mozillians account from Passwordless to Firefox Accounts?
1. In the following steps we assume you have 2FA set for your Firefox Accounts account. If not, see the steps from here. 2. Navigate to mozillians page and click Log In/Sign Up button. 3. Select “Continue with Firefox” method from mozillians login page.
4. Enter Firefox Accounts credentials.
5. Enter 2fa code from your application.
6. Navigate to Settings -> Profile Identities section, and verify that Firefox Accounts is set as your login identity. That means this is the only account you can use from now on to login to mozillians.
7. Trying to login with email to Mozillians will return an error page, asking to login with Firefox Accounts.
Q: How can I upgrade my mozillians account from passwordless to LDAP?
1. Login to mozillians with your email.
2. Navigate to profile settings page.
3. Scroll down to “Profile Identities” section and click “Add Identity” button.
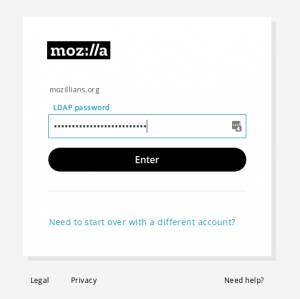
4. Enter your LDAP email in the "Log in with email" field and click "Enter" button.
5. Enter your LDAP password and click "Enter" button.
6. Enter 2fa code from your application and click "Log In" button.
7. Verify that success message is displayed, after adding the new LDAP identity.
8. Scroll down to “Profile Identities” section and verify that your LDAP account is set as your login identity. That means this is the only account you can use from now on to login to mozillians.
Q: What happens if I lose access to my LDAP (aka leave Mozilla) and I still need to be able to login as a community member?
When the LDAP account goes away, we will de-provision that identity from your Auth0 identity. This way you will be able to log in using other authentication providers (e.g. Github, Google or passwordless email). In order to do that you should add at least one such "secondary identity" to your profile while you are a staff member.
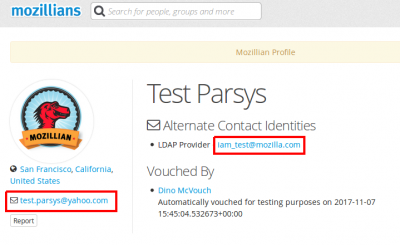
Q: I am a Mozilla staff member and I want to show my personal email address on my Mozillians profile. How do I do that?
1. Login to mozillians using your LDAP credentials.
2. Navigate to mozillians profile settings page.
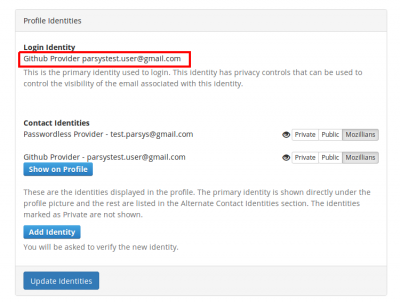
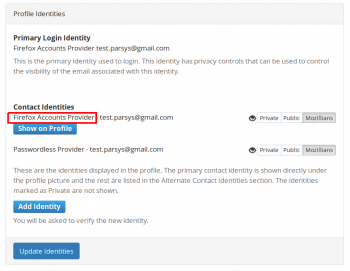
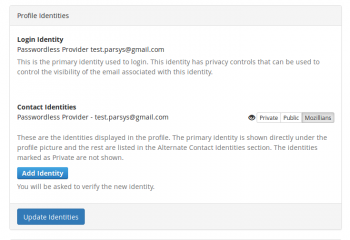
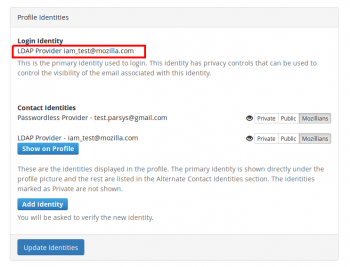
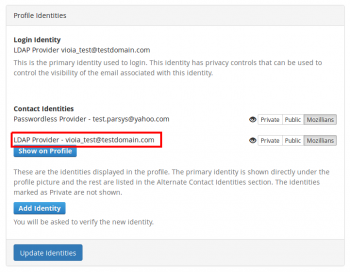
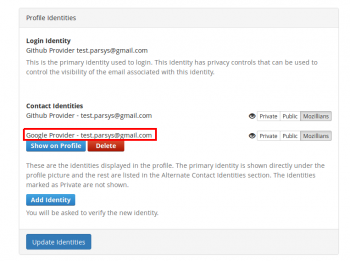
3. In Profile Identities section, Contact Identities sub-section shows the identities associated with your profile.
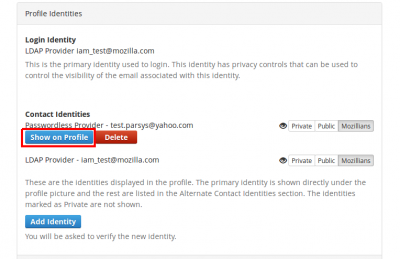
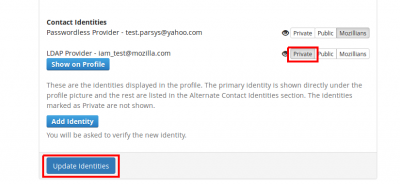
In order to set a certain email to show on your mozillians profile, you need to click the "Show on Profile" button corresponding to that email.
4. Success message should be displayed.
5. Now your primary email is displayed under the profile picture and your LDAP is shown in the "Alternate Contact Identities" section of your mozillians profile.
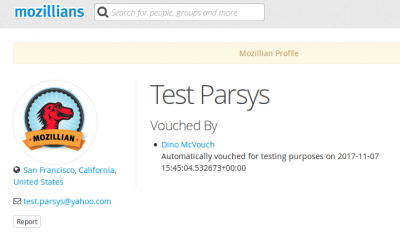
6. If you want your LDAP to not be shown at all on your profile, you should set your LDAP identity as Private and click Update Identities button.
7. Now only your personal email is shown on your profile, under the profile picture.
Q: I am a volunteer and I own a volunteer LDAP account. How can I upgrade my mozillians account from email (passwordless) login?
If you own a volunteer LDAP account, then you can upgrade your mozillians profile to that LDAP account (instead of github with 2FA), by following the next steps:
1. Login with email to mozillians.
2. Navigate to mozillians profile settings page.
3. Scroll down to “Profile Identities” section and click “Add Identity” button.
4. Enter your LDAP email in the "Log in with email" field and click "Enter" button.
5. Enter your LDAP password and click "Enter" button.
6. Enter 2fa code from your application and click "Log In" button.
7. Verify that success message is displayed, after adding the new LDAP identity.
8. Scroll down to “Profile Identities” section and verify that your volunteer LDAP account is set as your login identity. That means this is the only account you can use from now on to login to mozillians.
Q: How can I verify a google account in mozillians?
1. Login to mozillians.
2. Navigate to mozillians profile settings page.
3. Scroll down to “Profile Identities” section and click “Add Identity” button.
5. Select "Log in with Google" in the next page.
6. Enter your google email, then click Next.
7. Enter your google password, then click Next.
8. Verify that success message is displayed, after adding the new Google identity.
9. Scroll down to “Profile Identities” section and verify that your Google account is in your Contact identities section.
Q: What issues I might encounter by upgrading to Firefox Accounts?
There are some known issues with using Firefox Accounts in Mozilla IAM:
1. Login with Firefox Accounts is unavailable from inside some Android applications, including IRCCloud and Slack. This is due to lack of localStorage support in some Android WebViews. 2. Firefox Accounts can only be used in Mozilla IAM with 2FA enabled. Note that once you choose to use Firefox Accounts, it is required to set up 2FA, to avoid being locked out of your account.
Q: Why do the email login links expire after 15 minutes?
When you login using an email link, that link is valid for 15 minutes from when you request it. This expiration window of 15 minutes is driven both by security considerations and a desire for a positive user experience. The link is short lived so that there is a limited window of time during which a potential attacker could use the link if they were able to get access to it. This is especially important due to the inherently insecure nature of email transmission.
During the past 18+ months, experience shows that for a vast majority of users, this 15 minute expiration window has no effect on them as they receive the email link in their inbox mere seconds after they click the button requesting the link. Some users however do not receive the email login link immediately.
Short delays in delivery are just part of how email delivery works. Longer delays however can be caused by a feature called Greylisting. Continue on to the question below for further information on Greylisting.
Q: What is email Greylisting?
Some email providers institute Greylisting on all inbound email for their users as a measure to reduce spam. Greylisting temporarily rejects email from mail servers where the sender hasn't communicated with the recipient before or due to some other signal indicating the email may be spam. A mail server that is Greylisting expects that a valid sender and mail server will continue to retry sending the email over time and the Greylisting mail server will eventually accept the mail. In the case of a "transactional" email like the email login link, Greylisting prevents users from being able to do a real-time login.
Q: What can I do about my email provider's Greylisting?
Users who have email providers that use Greylisting will likely see this type of severely delayed transactional emails from other senders as well, for example when they sign up to a new web site and that web site sends them an email with a link to confirm that the user controls the email address they signed up with.
Unfortunately, in order for users with email providers that utilize Greylisting to work around this problem, they may need to contact their email provider or look in their providers documentation to see if there are whitelisting options available to them. There's nothing that Mozilla can do on the sending side to force the user's Greylisting mail server to accept and deliver the email.
Users sometimes ask to just increase the expiration time, for example to 30 or 60 minutes. We deliberately have not made this change because doing so would decrease our systems' security while not addressing the root cause of this problem (Greylisting). Instead, we ask that users either:
- contact their email provider to ask to have Greylisting disabled
- have Mozilla's domain, `sso.mozilla.com` whitelisted
- use an alternative login method to email links
- use an email address of a different email provider that doesn't employ Greylisting.
New Login Experience FAQ (Frequently Asked Questions)
Q: What if I want to use various identities in my browser sessions?
Please use Container Tabs to separate identities
Q: What if I want to switch my identity?
Please use Logout in the SSO Dashboard user menu. This is effectively a Mozilla IAM global logout.
Q: I have a Volunteer LDAP account but the New Login Experience sends me an email link.
This is a bug, please reach out to us via the IAM Discourse category.
Q: Auto-fill does not work with my password manager.
We tested the most common password managers successfully. In this case please reach out to us via the IAM Discourse category and let us know which password manager you use.
Q: I'm using the Slack app (or another app) and it only lets me login with a specific method (such as Firefox)
The Slack app does not let you use the back button when it tries to automatically login to SSO. If you had auto-login enabled, you also cannot force a logout as it's not within your web-browser.
This is a limitation of the app. In order to avoid this, you can make sure that you do not check automatic login. Otherwise, you can also delete the application's settings on your system and start the application again.
For Slack on macOS the settings are in ~/Library/Application Support/Slack - deleting this directory and restarting the Slack app will let you login normally again.