Inform/Distributed Denial of Service
This is an example of a page devoted to a specific technical issue. It should explain it clearly, with minimal jargon (and links to explain any necessary technical terms), and in a way unrelated to any specific legislation.
What is a DDOS?
The What Is section summarises the topic in three or four sentences, with a simple analogy.
A distributed denial of service attack (DDoS) occurs when multiple systems distributed around the Internet send a large volume of bogus requests to a targeted system or systems, usually one or more web servers. When a server is overloaded with connections or if its bandwidth is saturated, new connections can no longer be accepted or old ones maintained, thereby denying service to the website's legitimate visitors. It's like having a discussion in a small group, when a large mob surrounds you and they all begin shouting loudly. The real communication ceases, as it's lost in the noise.
Explanation
The Explanation section gives more detail, with diagrams and metaphors. It addresses common misconceptions. The inline links, explaining technical terms, would be to other Inform pages.
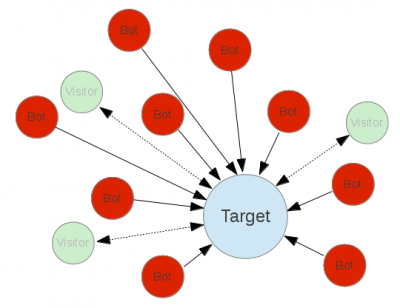
A DDoS attack is distributed, which means the attacker has control of a large number of systems around the Internet with which to attack. These would almost always be systems which have been compromised by malware and thereby probably also been joined to a botnet for control and coordination - so they are used without the consent of their owners. Attacks from a single or a small number of sources can be easily blocked by the target or their ISP. When an attack comes from many, many different IP addresses, it is hard to distinguish the malicious traffic from legitimate traffic, and so blocks run the risk of excluding real visitors.
If the plan is to saturate the target's bandwidth, they collectively need to have more outgoing bandwidth than the target servers have incoming bandwidth. If the attack instead attempts to exhaust the target server's resources such as memory or processing time, the attacker may need to analyse the site to find particular requests they can make which are resource-hungry (e.g. a search). Bugs or design flaws in the Internet infrastructure can give attackers ways to "amplify" their attacks - if you can find an infrastructure system which accepts a small incoming request and replies with a large response, and can persuade that system to send the response to the target instead of back to you, an attacker can use that ability to amplify the size of the attack beyond the amount of bandwidth they directly control.
DDoS attacks, particularly bandwidth exhaustion attacks, do not only affect the target site; they will also degrade the performance of other machines nearby on the network, because those machines share some of the saturated network links.
The most common motives for launching a DDoS attack are anger/revenge, extortion and 'the lulz'. Revenge or anger might be in response to the actions of some individual, company or organization which the attacker dislikes - it can be something as trivial as being beaten at an online game. Extortion by criminal gangs has been observed, particularly in the gambling industry - they send a threat and, if money is not paid, launch the DDoS, which costs the company money as they can't serve their customers. And attackers with the capability to do so may DDoS a site simply for the fun of it, in an action akin to vandalism.
Because the attacker is often anonymous and can be controlling the DDoS from anywhere in the world, legal action is unlikely to be effective against such an attack. The best mitigations are well-designed servers, hardware firewalls, competent technical staff, and a capable and responsive web hosting service and ISP.
Further Reading and Resources
The Further Reading and Resources section gives links to presentation slides, images, videos or other useful explanatory content.