Wiki/Bugzilla integration: https://github.com/LegNeato/mediawiki-bugzilla
Critical or Blocking NSS Bugs
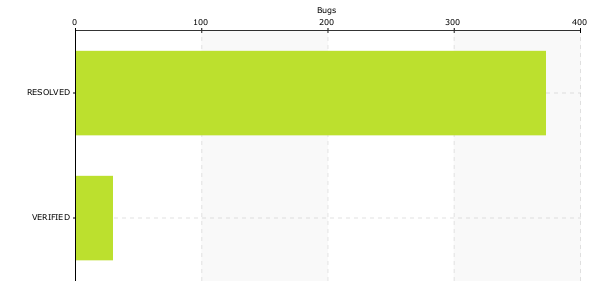
Critical NSS Bug Status Chart
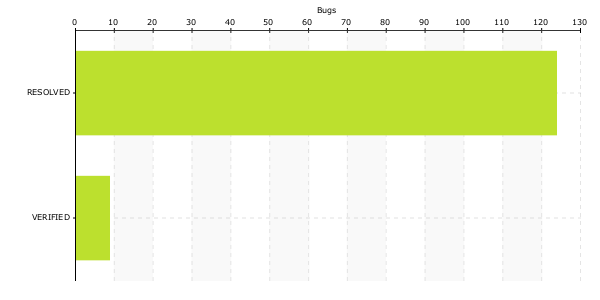
Blocking NSS Bug Status Chart
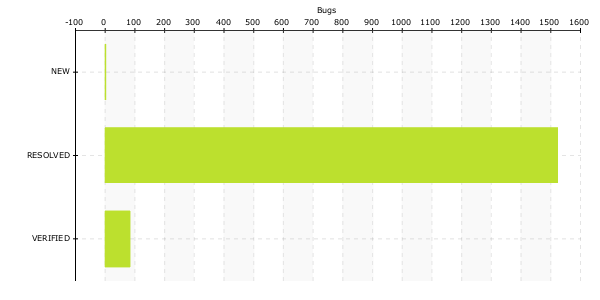
NEW Critical or Blocking NSS Bugs
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
Unconfirmed Critical or Blocking NSS Bugs
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
Assigned or Re-Opened Critical or Blocking NSS Bugs
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
P1 NSS Bugs
New NSS P1 Bugs
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
Assigned NSS P1 Bugs
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
No results.
0 Total;
0 Open (0%);
0 Resolved (0%);
0 Verified (0%);
NSS Bugs Changed in the last month
Full Query
| ID |
Summary |
Priority |
Status |
| 192264 |
Checkpoint NG Client root certificate issue |
P3 |
ASSIGNED |
| 671088 |
Allow certutil basic constraints to be specified on the command line |
P5 |
NEW |
| 1102981 |
secutil.c:2706:11: warning: incompatible pointer types passing 'int (FILE *, const SECItem *, const char *, int)' to parameter of type 'SECU_PPFunc' (aka 'int (*)(FILE *, SECItem *, char *, int)') [-Wincompatible-pointer-types] (for SECU_PrintCertificate) |
P5 |
RESOLVED |
| 1159216 |
Support PKCS8 import for private (EC)DH keys without a public key |
P5 |
RESOLVED |
| 1548723 |
Certificate compression |
P3 |
RESOLVED |
| 1648172 |
[meta] Tools: certutil, strsclnt, selfserv, vfychain, vfyserv should use mozilla::pkix |
P3 |
NEW |
| 1763237 |
[meta] Thread safety issues in NSS |
P2 |
NEW |
| 1781275 |
Consider integration of TLS Anvil into CI |
P3 |
NEW |
| 1833596 |
Add a lint for banned functions |
P3 |
NEW |
| 1869753 |
DTLS doesn't currently support ECH |
P5 |
NEW |
| 1871629 |
[meta] Kyber support |
P3 |
ASSIGNED |
| 1874451 |
DTLS failures in Tls12ServerXyber768d00NotSupported gtest |
P3 |
RESOLVED |
| 1883321 |
[meta] E2ES - Messaging Layer Security - Implement an MLS interface via XPCOM and a system module |
-- |
ASSIGNED |
| 1894457 |
import PKCS#12 file with ED25519 private key |
-- |
UNCONFIRMED |
| 1900537 |
[meta] E2ES - Messaging Layer Security - Implement a prototype Web API |
-- |
ASSIGNED |
| 1910172 |
Perma documentation subprocess.CalledProcessError: Command '['/builds/worker/.mozbuild/srcdirs/gecko-8a5b87fe5d69/_virtualenvs/docs/bin/python', 'doc', '--outdir', 'docs-out', '--no-open', '--no-serve', '--archive', '--fatal-warnings', '--check-num-warnin |
P5 |
RESOLVED |
| 1910370 |
Assertion failure: ss->ssl3.hs.dtls13ClientMessageBuffer.len == 0, at ../../lib/ssl/ssl3con.c:5668 |
-- |
RESOLVED |
| 1912052 |
Continuously update corpus for NSS in OSS-Fuzz |
-- |
RESOLVED |
| 1913047 |
Certificate chain validation problem |
-- |
RESOLVED |
| 1915274 |
Clean up documentation warnings in NSS |
-- |
NEW |
| 1915614 |
RSA-MIN=2049 doesn't let me use a 2049-bit RSA certificate, similarly with other odd sizes |
P5 |
UNCONFIRMED |
| 1915792 |
Allow NSS to import pkcs8 keys that are missing the public key part |
-- |
RESOLVED |
| 1923002 |
Extract certficates with handshake collection script |
-- |
RESOLVED |
| 1923004 |
Use DTLS with handshake collection script |
-- |
ASSIGNED |
| 1923006 |
Set `len_control` option for fuzz targets |
-- |
RESOLVED |
| 1923037 |
Integrate CryptoFuzz in NSS CI |
-- |
ASSIGNED |
| 1923038 |
Remove mpi_* fuzz targets |
-- |
ASSIGNED |
| 1923280 |
tstclnt memory leak in dumpCertificatePEM |
-- |
RESOLVED |
| 1923285 |
Update ACVP docker libraries |
P5 |
NEW |
| 1924774 |
Enable ssl_grp_kem_mlkem768x25519 for WebRTC DTLS1.3 |
P3 |
RESOLVED |
| 1925056 |
NSS gtests filter cleans up the constucted buffer before the use |
P2 |
NEW |
| 1925503 |
Thread safety of `ssl_isInited` in `ssl_Init` |
P3 |
RESOLVED |
| 1925505 |
Thread safety of `firsttime` in `ssl_SetDefaultsFromEnvironment` |
P3 |
RESOLVED |
| 1925512 |
Thread safety of `lockStatus` and `locksEverDisabled` |
P3 |
ASSIGNED |
| 1925975 |
NSS 3.106 source distribution should include NSPR 4.36 |
-- |
NEW |
| 1926302 |
Debugging NSS with pernosco |
-- |
NEW |
| 1926548 |
extend expiration time for CI artifacts |
-- |
NEW |
| 1927096 |
nss-3.106 fails tests (pk12util: PKCS12 decode not verified: SEC_ERROR_BAD_PASSWORD: The security password entered is incorrect.) |
P5 |
UNCONFIRMED |
| 1927351 |
SSLKEYLOG support for Encrypted Client Hello |
-- |
UNCONFIRMED |
| 1927797 |
Certificate Compression for QUIC |
P2 |
UNCONFIRMED |
| 1928402 |
NSS is missing the release notes for 3.105 |
P5 |
NEW |
| 1929041 |
Choose random tstclnt args for handshake collection script |
-- |
ASSIGNED |
42 Total;
27 Open (64.29%);
15 Resolved (35.71%);
0 Verified (0%);


