SummerOfCode/2013/SecurityReport/WeeklyUpdates/2013-07-22
Jump to navigation
Jump to search
This Week
- This week I collected information about various security related headers and added reporting about them in the security report tool.
- CSP Headers
- Websites can set any one of these header to send CSP policy. CSP policy is used to protect web users from content injection attacks and it loads resources only from trusted sources.
- CSP specification is under development and websites use different headers to send their CSP policy. For example, "X-Content-Security-Policy", "Content-Security-Policy", "X-WebKit-CSP".
- According to standard website should send CSP policy using "Content-Security-Policy" header. and other two headers are browser specific.
- I added observer on "http-on-receive-response" to monitor HTTP/S responses. In that listener I check for the presence of various HTTP headers.
- CSP Headers
- X-Frame-Options Header
- I also read about "X-Frame-Options" header and checked whether it is used by website or not. If not then appropriate message is displayed in the security report tool's "Sec-Headers" Tab. Absent of "X-Frame-Option" header means site is vulnerable to Clickjacking attacks.
- X-Frame-Options Header
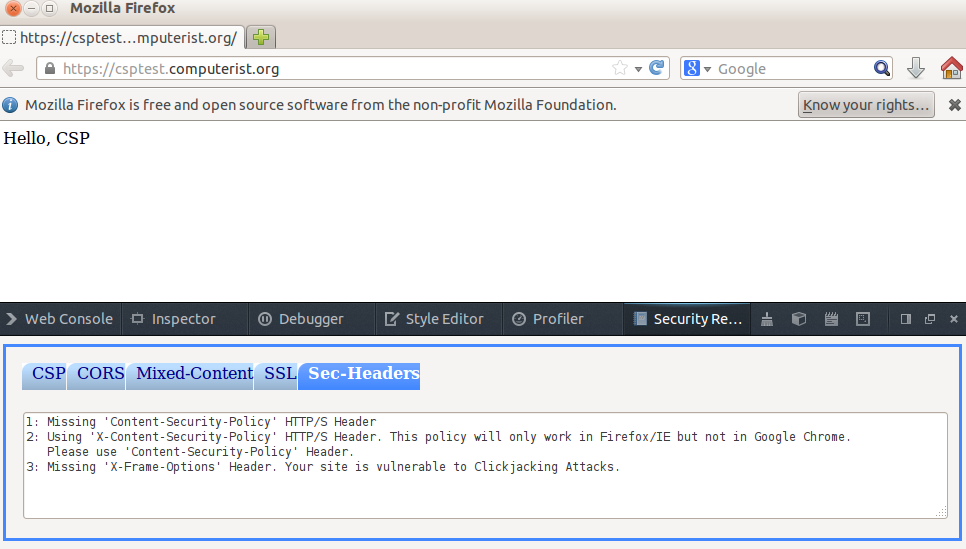
- Following figure shows CSP and X-Frame-Option headers detected by security report tool and shown appropriate messages in the "Sec-Headers" tab. Currently displayed messages are tentative and we will display more comprehensive messages. I will discuss with mentor about what messages to display and will update it accordingly.