User:Fbraun/HawkSecurity
From MozillaWiki
Hawk Overview
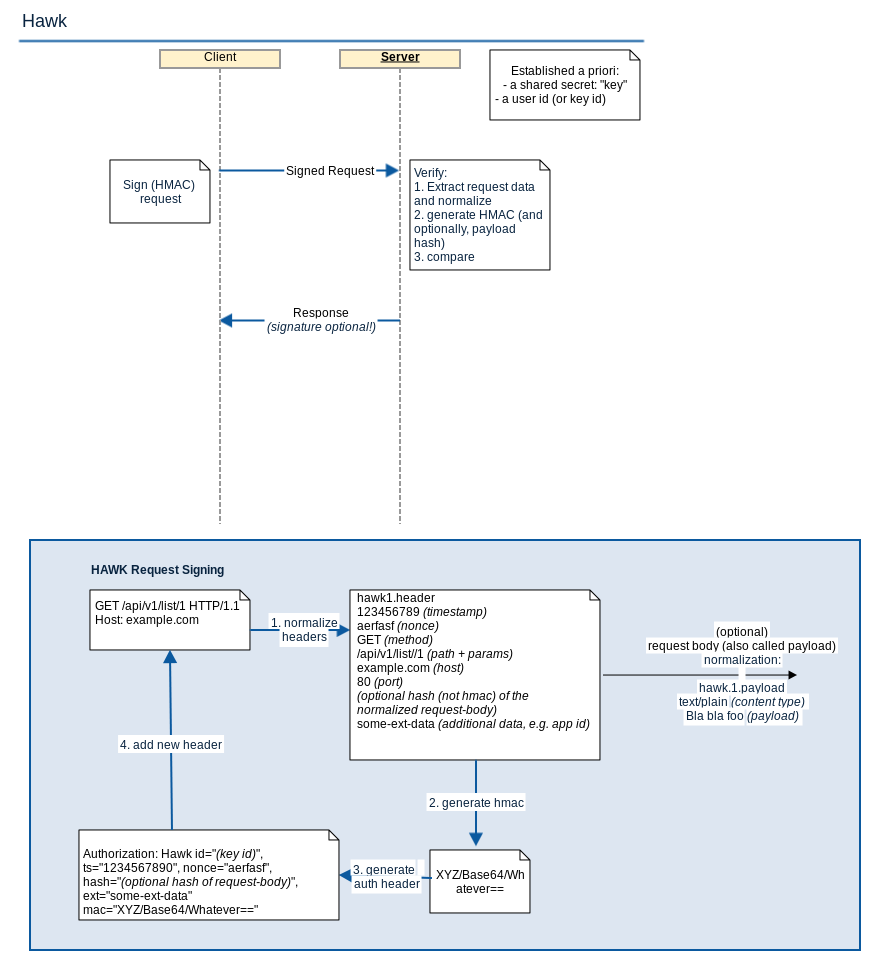
Hawk provides lightweight authentication for HTTP requests: Assuming a shared secret Server and Client can verify the authenticity of HTTP request and response data (using an HMAC). However, Hawk does not provide confidentiality and only some HTTP headers are signed (Host and Content-Type (optionally)). See also the diagram below for more information.
Hawk Security
- no confidentiality
- key sharing is different for each application
- MITM possible, if not using TLS
- a man in the middle can permanently DoS, by suggesting the client a permanent redirect (HTTP 301)
- See also the excellent security section at the Hawk project page
Resulting Suggestions
- do not use HAWK without TLS. Require TLS for all requests and responses
- new HMAC for each session, and not permanent per user
- derive HMAC instead of sending it directly through the TLS connection. FxA uses the session token for this.
- enable payload validation in client and server
Review tips
- the secret key has to be shared between client and server. How does the tested application do this?