Security/Web Bug Rotation: Difference between revisions
(Adding boilerplate comment to add once the bug is fixed) |
|||
| (34 intermediate revisions by 10 users not shown) | |||
| Line 1: | Line 1: | ||
{{TOC right}} | |||
= | = Web Bug Verification = | ||
Web security bugs are reported to security@Mozilla.org mailbox or in a Bugzilla component, a member of Mozilla Security verifies the reported vulnerability before passing the bug on to developers. This verification work is shared by several members of the security team. The following pages meant to document the procedures for verification and to serve as a reminder for those "on call for the week"as to the procedures that need to be completed. In general bugs will have an attempt to verify them in approximately 1 working day. | |||
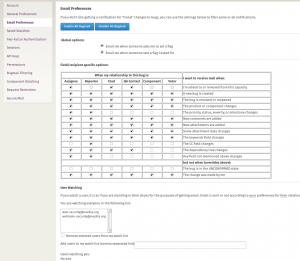
To track bug submissions, set your bugzilla preferences to follow users "web-security@mozilla.org" and | |||
"webtools-security@mozilla.org": | |||
# | [[File:Bug bounty watch.png|thumbnail|left]] | ||
# | |||
# | |||
# | <br /><br /><br /><br /><br /><br /><br /><br /><br /> | ||
= Rotation = | |||
# | {| class="wikitable" | ||
## | |- | ||
# | ! Day !! On-call !! Slack handle | ||
# | |- | ||
| Monday - Friday || Frida Kiriakos || Frida | |||
|} | |||
= Verification process = | |||
The procedure below is performed by the on-call individual. | |||
# If the issue was reported to the security@ alias, create a bug for it | |||
# Determine if the issue reported is NEW, INVALID, or DUPLICATE | |||
# For '''NEW''' bugs | |||
## CC the Security POC and Backup on the website [https://docs.google.com/spreadsheets/d/14Gp6TPAibO7UkgJTXSeOIeFNMdfDbrUXQpqRFW3tDbg/edit#gid=0 contact list]. | |||
## Change status to ASSIGNED. Edit "Assigned To" and assign the bug to the Security POC. | |||
## Needinfo flag the Security POC and their backup. | |||
## Set the right '''[https://bugzilla.mozilla.org/describekeywords.cgi keywords]''' | |||
### sec-{critical,high,moderate,low,other}, see [https://wiki.mozilla.org/WebAppSec/Web_App_Severity_Ratings#Severity_Ratings severity ratings] | |||
### wsec-{authentication,cookie,xss,sqli,...}, see [https://wiki.mozilla.org/WebAppSec/Web_App_Severity_Ratings#Group_Keywords vulnerability types] | |||
### If the bug is rated sec-high or sec-critical, or if you believe the issue warrants it, cc the Site Owner and Business Owner to the bug, cc and needinfo flag them. | |||
# If the verification shows that the issue is invalid, close the bug as '''INVALID''' | |||
# For '''DUPLICATE''' bugs, set dupe against old bug. Set keywords & whiteboard for the new duped bug | |||
Follow up on a '''NEW''' bug until you get the assurance that it will be fixed, the urgency of which depends on the vulnerability and the target. | |||
= Vulnerability Mitigation process = | |||
When the reported vulnerability is mitigated, the engineer that did the work should change the bug status from '''NEW''' to '''FIXED'''. The engineer or bug bounty triager should then add a comment to the bug so the reporter knows what happens next. That comment should be | |||
<blockquote> | |||
Thanks very much for reporting this issue to us. Now that the issue is fixed, the bug bounty team will be reviewing your report over the upcoming weeks to make a determination of what if any award Mozilla will be granting for this report. It may take up to 3 weeks but know that we've not forgotten this ticket, we have a tracking system and a review cadence that will ensure that all potentially bounty eligible reports get reviewed and acted on. | |||
</blockquote> | |||
=Bounty= | |||
# Bounty flags are set automatically through the [https://bugzilla.mozilla.org/form.web.bounty Web Bounty Form]. | |||
# Check the Web Bounty FAQ for whether the site and service are in scope for the bounty program. | |||
## If the site is not on the [https://www.mozilla.org/en-US/security/bug-bounty/faq-webapp/#eligible-bugs eligible list] and the bug is not "extraordinary" please note that in the whiteboard field (e.g. "[bounty-ineligible site]") | |||
# If a submitter requests that a bug submitted outside the automated form have a bounty flag added, set the bounty flag to "?" | |||
For '''NEW''' bugs | |||
== NEW == | |||
For NEW bugs that have been verified, simply set the "sec-bounty" flag to "?" | |||
Most new eligible bugs are now submitted through the https://bugzilla.mozilla.org/form.web.bounty bounty form. For these bugs the appropriate flag will already be set. | |||
== DUPLICATE == | |||
If the bug is a duplicate of an existing bug | |||
# Set "sec-bounty" flag to "-" on new bug since it was a dupe (as long as it is duped to an OLDER bug). | |||
# Set the new bug blocking the appropriate metabug(s) | |||
#* For older bugs duped against that do not have the current flags | #* For older bugs duped against that do not have the current flags | ||
## If the old bug has the attachment 'bounty non-qual' or similar then set sec-bounty- on the old bug | ## If the old bug has the attachment 'bounty non-qual' or similar then set sec-bounty- on the old bug | ||
## If the old bug has the attachment 'bounty awarded X' or 'bounty paid X', then set sec-bounty+ on the old bug | ## If the old bug has the attachment 'bounty awarded X' or 'bounty paid X', then set sec-bounty+ on the old bug | ||
## | ## If no duplicate is found and the issue is not verified the bug shall be RESOLVED - INVALID and the whiteboard tag removed. | ||
Latest revision as of 22:45, 29 April 2022
Web Bug Verification
Web security bugs are reported to security@Mozilla.org mailbox or in a Bugzilla component, a member of Mozilla Security verifies the reported vulnerability before passing the bug on to developers. This verification work is shared by several members of the security team. The following pages meant to document the procedures for verification and to serve as a reminder for those "on call for the week"as to the procedures that need to be completed. In general bugs will have an attempt to verify them in approximately 1 working day.
To track bug submissions, set your bugzilla preferences to follow users "web-security@mozilla.org" and "webtools-security@mozilla.org":
Rotation
| Day | On-call | Slack handle |
|---|---|---|
| Monday - Friday | Frida Kiriakos | Frida |
Verification process
The procedure below is performed by the on-call individual.
- If the issue was reported to the security@ alias, create a bug for it
- Determine if the issue reported is NEW, INVALID, or DUPLICATE
- For NEW bugs
- CC the Security POC and Backup on the website contact list.
- Change status to ASSIGNED. Edit "Assigned To" and assign the bug to the Security POC.
- Needinfo flag the Security POC and their backup.
- Set the right keywords
- sec-{critical,high,moderate,low,other}, see severity ratings
- wsec-{authentication,cookie,xss,sqli,...}, see vulnerability types
- If the bug is rated sec-high or sec-critical, or if you believe the issue warrants it, cc the Site Owner and Business Owner to the bug, cc and needinfo flag them.
- If the verification shows that the issue is invalid, close the bug as INVALID
- For DUPLICATE bugs, set dupe against old bug. Set keywords & whiteboard for the new duped bug
Follow up on a NEW bug until you get the assurance that it will be fixed, the urgency of which depends on the vulnerability and the target.
Vulnerability Mitigation process
When the reported vulnerability is mitigated, the engineer that did the work should change the bug status from NEW to FIXED. The engineer or bug bounty triager should then add a comment to the bug so the reporter knows what happens next. That comment should be
Thanks very much for reporting this issue to us. Now that the issue is fixed, the bug bounty team will be reviewing your report over the upcoming weeks to make a determination of what if any award Mozilla will be granting for this report. It may take up to 3 weeks but know that we've not forgotten this ticket, we have a tracking system and a review cadence that will ensure that all potentially bounty eligible reports get reviewed and acted on.
Bounty
- Bounty flags are set automatically through the Web Bounty Form.
- Check the Web Bounty FAQ for whether the site and service are in scope for the bounty program.
- If the site is not on the eligible list and the bug is not "extraordinary" please note that in the whiteboard field (e.g. "[bounty-ineligible site]")
- If a submitter requests that a bug submitted outside the automated form have a bounty flag added, set the bounty flag to "?"
For NEW bugs
NEW
For NEW bugs that have been verified, simply set the "sec-bounty" flag to "?" Most new eligible bugs are now submitted through the https://bugzilla.mozilla.org/form.web.bounty bounty form. For these bugs the appropriate flag will already be set.
DUPLICATE
If the bug is a duplicate of an existing bug
- Set "sec-bounty" flag to "-" on new bug since it was a dupe (as long as it is duped to an OLDER bug).
- Set the new bug blocking the appropriate metabug(s)
- For older bugs duped against that do not have the current flags
- If the old bug has the attachment 'bounty non-qual' or similar then set sec-bounty- on the old bug
- If the old bug has the attachment 'bounty awarded X' or 'bounty paid X', then set sec-bounty+ on the old bug
- If no duplicate is found and the issue is not verified the bug shall be RESOLVED - INVALID and the whiteboard tag removed.