Project Fission: Difference between revisions
No edit summary |
(fission is no longer a nightly experiment) |
||
| (73 intermediate revisions by 17 users not shown) | |||
| Line 1: | Line 1: | ||
Fission is Mozilla's implementation of ''Site Isolation'' in Firefox. Site Isolation is a security feature that offers additional protection in case of large classes of security bugs. Site Isolation safely sandboxes web pages and web frames, isolating them from each other, further strengthening Firefox security. | |||
= Why? = | |||
Web security is designed in such a way that websites or webframes cannot access each other's data inside the browser. However, bugs happen. The Firefox teams and the Mozilla security teams invest considerable effort in avoiding security bugs, or, if they exist, finding them out and fixing them before release. However, if a bug somehow slips past developers, analysis and tests, and a sufficiently cunning attacker manages to find the bug before it can be fixed, they can sometimes craft a page specifically designed to access data from other sites that the user is currently visiting or has recently visited. | |||
Firefox developers already employ a number of counter-measures to make such undetected bugs less likely to succeed, from programming in memory-safe languages to adopting defensive programming techniques. Site Isolation is a new counter-measure dedicated to this purpose. With Site Isolation, pages and frames are executed in processes dedicated to their origin. | |||
= Example = | |||
Consider a blog on https://example.com with a Facebook like button (frame from https://facebook.com) and a Twitter button (frame from https://twitter.com). Without Site Isolation, this entire page runs in a single process. If an undetected bug in Firefox somehow allows the main page of the blog to access data inside the frames despite the protections in place, the malicious owner of https://example.com (or someone who had already stolen the domain) may be able to take advantage of this bug to impersonate the Firefox user in the Facebook and Twitter frames, and possibly use this impersonation to send fake messages or read private messages. | |||
With Site Isolation, this blog now runs on three different processes, one for https://example.com, one for https://facebook.com and one for https://twitter.com. These processes are sandboxed which limits what each of the processes can do. Even if the malicious owner of https://example.com were to take advantage of an undetected Firefox bug and to take control of the process in charge of https://example.com, the processes in charge of https://facebook.com or https://twitter.com would reject any request from this compromised process. In other words, this hypothetical bug is not sufficient anymore to impersonate the Firefox user in the Facebook and Twitter frames. | |||
= Contact = | |||
[https:// | The Fission team is standing by, ready to answer your questions in the '''#fission:mozilla.org''' room on [https://chat.mozilla.org/#/room/#fission:mozilla.org Mozilla's Matrix server]. | ||
= Observing Fission = | |||
In desktop Firefox, you may open '''about:processes''' to see the processes used by Firefox. | |||
= Reporting Bugs = | |||
[https://bugzilla.mozilla.org/ | To file a Fission bug in Bugzilla, [https://bugzilla.mozilla.org/enter_bug.cgi?product=Core&bug_type=defect&short_desc=%5bFission%5d&blocked=fission-dogfooding click here to use this Fission bug template]. Or file a bug and include the word “Fission” in the bug summary. The Fission team’s bug triage will find the bug, regardless of which Bugzilla component you file it in. | ||
[https://bugzilla.mozilla.org/ | * Fission meta {{bug|1451850}} | ||
* [https://bugzilla.mozilla.org/buglist.cgi?classification=Client%20Software&classification=Developer%20Infrastructure&classification=Components&classification=Server%20Software&classification=Other&f1=cf_fission_milestone&resolution=---&o1=anywordssubstr&query_format=advanced&v1=M4.1%2CM5%2CM6 All bugs blocking Fission Nightly] | |||
= Enabling Fission = | |||
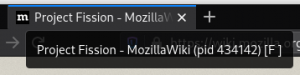
[ | [[File:Fission tab tooltip.png|thumb|A "[F]" in a loaded tab's tooltip indicates that Fission is enabled]] | ||
Fission was released to desktop [https://www.mozilla.org/firefox/95.0/releasenotes/ Firefox in version 95]. | |||
# In ''about:config'', set the '''"fission.autostart"''' and '''"gfx.webrender.all"''' prefs to '''"true"'''. DO NOT edit any other "fission.*" or "gfx.webrender.*" prefs. | |||
You can verify that Fission has been enabled by hovering over the current tab. If the tooltip contains a "[F]", Fission is enabled. Background tabs' tooltips might not have the "[F]" if they are not loaded yet. | |||
=== Disabling Fission === | |||
If you encounter an issue while using Fission, it can be useful to create a new profile in about:profiles and attempt to recreate the issue. This can be useful to determine if issues are Fission-specific. If you encounter an issue that only happens with Fission, please be sure to file a bug in Bugzilla about it as described above! | |||
To disable Fission, set the "fission.autostart" pref to "false" and restart Firefox. | |||
= Sub-pages = | |||
[ | * [[Project Fission/Memory|Memory]] | ||
* [[Project_Fission/FrontEnd|FrontEnd]] | |||
* [[Project_Fission/Enabling_Tests_with_Fission|Enabling Tests with Fission]] | |||
* [[Project Fission/DocShell_Tree_Replace|Fix out-of-process uses of DocShell tree and nsIDocShellTreeItem]] | |||
* | * [[Project Fission/BrowsingContext|In progress BrowsingContext documentation]] | ||
Latest revision as of 16:59, 17 March 2022
Fission is Mozilla's implementation of Site Isolation in Firefox. Site Isolation is a security feature that offers additional protection in case of large classes of security bugs. Site Isolation safely sandboxes web pages and web frames, isolating them from each other, further strengthening Firefox security.
Why?
Web security is designed in such a way that websites or webframes cannot access each other's data inside the browser. However, bugs happen. The Firefox teams and the Mozilla security teams invest considerable effort in avoiding security bugs, or, if they exist, finding them out and fixing them before release. However, if a bug somehow slips past developers, analysis and tests, and a sufficiently cunning attacker manages to find the bug before it can be fixed, they can sometimes craft a page specifically designed to access data from other sites that the user is currently visiting or has recently visited.
Firefox developers already employ a number of counter-measures to make such undetected bugs less likely to succeed, from programming in memory-safe languages to adopting defensive programming techniques. Site Isolation is a new counter-measure dedicated to this purpose. With Site Isolation, pages and frames are executed in processes dedicated to their origin.
Example
Consider a blog on https://example.com with a Facebook like button (frame from https://facebook.com) and a Twitter button (frame from https://twitter.com). Without Site Isolation, this entire page runs in a single process. If an undetected bug in Firefox somehow allows the main page of the blog to access data inside the frames despite the protections in place, the malicious owner of https://example.com (or someone who had already stolen the domain) may be able to take advantage of this bug to impersonate the Firefox user in the Facebook and Twitter frames, and possibly use this impersonation to send fake messages or read private messages.
With Site Isolation, this blog now runs on three different processes, one for https://example.com, one for https://facebook.com and one for https://twitter.com. These processes are sandboxed which limits what each of the processes can do. Even if the malicious owner of https://example.com were to take advantage of an undetected Firefox bug and to take control of the process in charge of https://example.com, the processes in charge of https://facebook.com or https://twitter.com would reject any request from this compromised process. In other words, this hypothetical bug is not sufficient anymore to impersonate the Firefox user in the Facebook and Twitter frames.
Contact
The Fission team is standing by, ready to answer your questions in the #fission:mozilla.org room on Mozilla's Matrix server.
Observing Fission
In desktop Firefox, you may open about:processes to see the processes used by Firefox.
Reporting Bugs
To file a Fission bug in Bugzilla, click here to use this Fission bug template. Or file a bug and include the word “Fission” in the bug summary. The Fission team’s bug triage will find the bug, regardless of which Bugzilla component you file it in.
- Fission meta bug 1451850
- All bugs blocking Fission Nightly
Enabling Fission
Fission was released to desktop Firefox in version 95.
- In about:config, set the "fission.autostart" and "gfx.webrender.all" prefs to "true". DO NOT edit any other "fission.*" or "gfx.webrender.*" prefs.
You can verify that Fission has been enabled by hovering over the current tab. If the tooltip contains a "[F]", Fission is enabled. Background tabs' tooltips might not have the "[F]" if they are not loaded yet.
Disabling Fission
If you encounter an issue while using Fission, it can be useful to create a new profile in about:profiles and attempt to recreate the issue. This can be useful to determine if issues are Fission-specific. If you encounter an issue that only happens with Fission, please be sure to file a bug in Bugzilla about it as described above!
To disable Fission, set the "fission.autostart" pref to "false" and restart Firefox.