Security/Reviews/F1: Difference between revisions
Jump to navigation
Jump to search
| Line 55: | Line 55: | ||
| Intrusion Monitoring requirements may impact privacy requirements||Develop CEF logging points that capture the data needed to monitor the environment properly without retaining privacy impacting data.||Government / Lawyers||9||3||||3||Violation of our privacy policies|| | | Intrusion Monitoring requirements may impact privacy requirements||Develop CEF logging points that capture the data needed to monitor the environment properly without retaining privacy impacting data.||Government / Lawyers||9||3||||3||Violation of our privacy policies|| | ||
|- | |- | ||
| Unauthorized or unexpected | | Unauthorized or unexpected code or system change could have a significant compliance and policy implication||Ensure strong change control practices are implemented, and detective controls such as file system integrity and audit logging are implemented. Ensure that any code change that modifies interactions between the client and the server, or the server and third parties is reviewed and signed off by security, IT, DEV before they hit production.||Malicious Insider / Skilled Attacker||6||3||||2||Violation of our privacy policies, potential exposure to new vulnerabilities|| | ||
|- | |- | ||
| Subpoenas/NSLs could force Mozilla to disclose logs of user communications||Ensure that reasonable data retention limits are observed. Anonymize source and destination data, limit the collection of log data to information necessary to maintain and develop the service. If push come to shove, shut down service. ||Government / Lawyers||8||2||||4||Violation of our privacy policies, and major reputational damage.|| | | Subpoenas/NSLs could force Mozilla to disclose logs of user communications||Ensure that reasonable data retention limits are observed. Anonymize source and destination data, limit the collection of log data to information necessary to maintain and develop the service. If push come to shove, shut down service. ||Government / Lawyers||8||2||||4||Violation of our privacy policies, and major reputational damage.|| | ||
Revision as of 04:53, 4 May 2011
Background
Project Page
Bugzilla Review Trackers
Links
https://wiki.mozilla.org/Services/F1/Server/
https://wiki.mozilla.org/Services/F1/Server/API
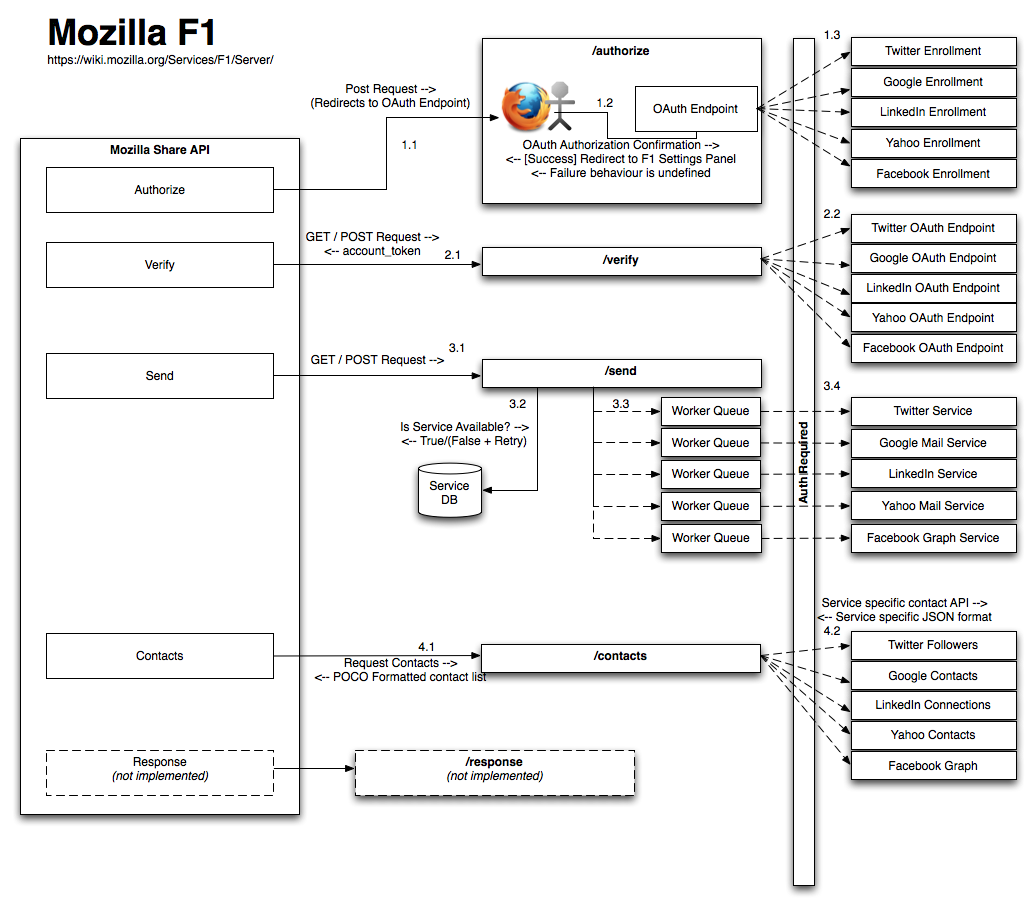
Architecture
Data Flow
Threat Model
| Threat | Proposed Mitigations | Threat Agent | Rating | Likelihood | Notes | Impact | Notes | Status |
| Compromise of consumer key could allow attackers to impersonate Mozilla to 3rd party services | Ensure that consumer keys are isolated from user interactive environments. Ideally the worker services should be isolated from the front end servers and share submission functions (further recommendations are available in the asynchronous architecture documentation) | Malicious Insider / Skilled Attacker | 6 | 2 | 3 | Attacker would be able to spoof Mozilla F1 to 3rd parties, but only on behalf of users | ||
| Compromise of server could permit ongoing collection of Oauth tokens for access to user accounts | Implement hardened environments and intrusion detection to reduce the likelihood of compromise. The f1 environment should be tightly segregated to prevent exfiltration of data to the extent possible. Ensure that tokens are held on the server only as long as strictly necessary, are not logged, and cleared before they are garbage collected. | Malicious Insider / Skilled Attacker | 8 | 2 | 4 | User accounts at 3rd party services would be compromised. | ||
| Oauth Tokens for some service are overly permissive (i.e. Google tokens grant full access) | [Out of Mozilla\'s Control] Document and advise users of the potential implications of abuse of the tokens. | Malicious Insider / Skilled Attacker | 15 | 5 | There are at least two of the services that suffer from this issue. | 3 | A compromised token for the affected services would allow full control over the account | |
| Compromise of the service will result in significant damage to Mozilla\'s reputation | Ensure that rehearsed Incident Response practices are in place. Have effective, clear, and open communication ready in case an incident occurs. Ensure that ownership and clear lines of responsibility exist for each component of the service. | Government / Media / Lawyers | 4 | 2 | 2 | |||
| 3rd Party Service Changes could render portions of F1 inoperable | Ensure that worker components that depend on communications with 3rd parties are isolated by process to prevent issues with one service affecting other components of F1 | Public Attacker | 6 | 3 | 2 | |||
| Users flooding service could exhaust API call limits | Implement rate limiting of share requests. Where possible, work with 3rd parties to improve notification of potential abuse. | Public Attacker | 8 | 4 | 2 | |||
| URL Shorteners get a copy of URLs shared by F1 Users | Implement a URL shortening service that is consistent with Mozillas privacy policy, or provide users the option of disabling URL shortening (this should be the default option on shares with a specific recipient list) | 3rd Party Service | 10 | 5 | 2 | Share urls are known to a 3rd party (bit.ly) | ||
| Intrusion Monitoring requirements may impact privacy requirements | Develop CEF logging points that capture the data needed to monitor the environment properly without retaining privacy impacting data. | Government / Lawyers | 9 | 3 | 3 | Violation of our privacy policies | ||
| Unauthorized or unexpected code or system change could have a significant compliance and policy implication | Ensure strong change control practices are implemented, and detective controls such as file system integrity and audit logging are implemented. Ensure that any code change that modifies interactions between the client and the server, or the server and third parties is reviewed and signed off by security, IT, DEV before they hit production. | Malicious Insider / Skilled Attacker | 6 | 3 | 2 | Violation of our privacy policies, potential exposure to new vulnerabilities | ||
| Subpoenas/NSLs could force Mozilla to disclose logs of user communications | Ensure that reasonable data retention limits are observed. Anonymize source and destination data, limit the collection of log data to information necessary to maintain and develop the service. If push come to shove, shut down service. | Government / Lawyers | 8 | 2 | 4 | Violation of our privacy policies, and major reputational damage. | ||
| MitM – Attacker between F1 Client and Server | Ensure that STS is used, disable HTTP on the server, ensure that chrome panes properly surface certificate errors. | Public Attacker (close to user) | 12 | 4 | 3 | An attacker can gain control of user account information, and the ability to modify shares in transit | ||
| MitM Attacks against F1 Server and 3rd parties | Ensure that all configured services use HTTPS. Work with 3rd party providers to ensure that all services used by F1 are able to be used via HTTPS if they cannot. Ensure that server code properly verifies certificates (python has issues with this). | Public Attacker / ISP / Government | 6 | 2 | 3 | An attacker would gain control over all user accounts that F1 interacts, and the ability to modify share requests destined for the affected service. | ||
| Phishing – A malicious site could impersonate the F1 Settings Page | Load the F1 settings page in a fashion that distinguishes it from a normal web site. | Public Attacker | 9 | 3 | 3 | Trick a user into granting a malicious service Oauth authorization | ||
| Chrome code injection | Code review and securtiy testing | Public Attacker | 8 | 2 | 4 | A chrome code injection flaw would allow an attacker to inject code into the browser at a high level of privilege. | ||