Identity/Watchdog/Password Age Visualizer
Password Age Visualizer
Features
This add-on adds a small red padlock icon to the add-on bar. Upon clicking, it opens a new page with a visualization on it.
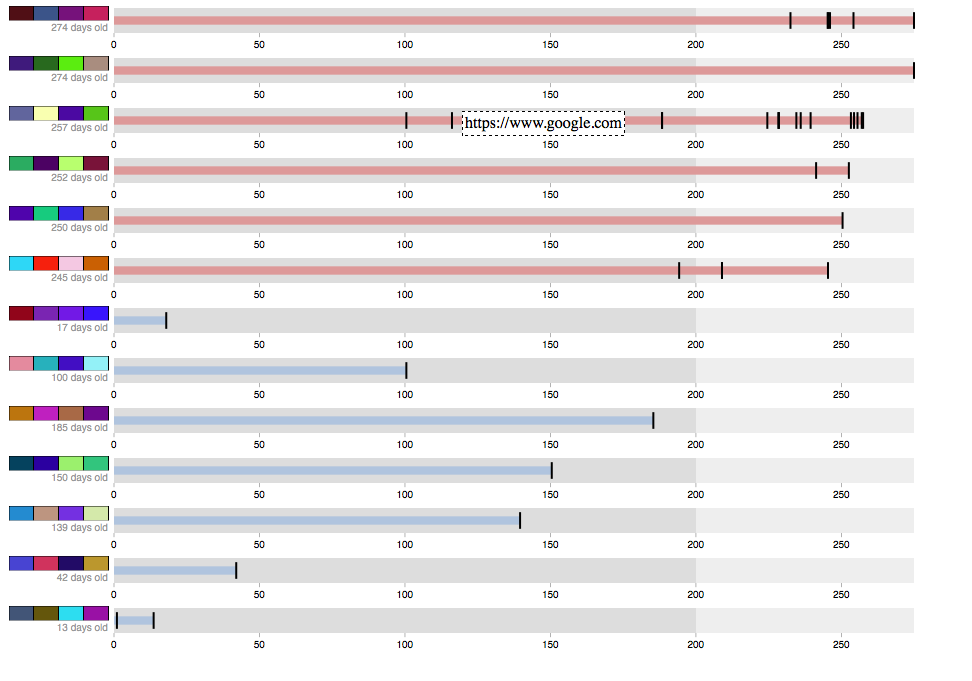
The graph visualization is generated with data from nsiLoginManager. It's a bullet visualization, as seen below.
Each row represents a password in use in a user's profile. A row of visual hashes is displayed to the left of each row. Underneath the hash is the "age" of the password in days. Age is defined here as the first time a password was used to sign up on a website. To the right, a bar extends rightward showing how many days the password has been in use. If the password is over 200 days old (the default recommended password age, in this case) the bar turns red, indicating that it's time to stop using that password.
On each bar there are several black markers. Hovering over one will display the name of the site that the given password was used at that point in time.
Clicking on a visual hash will prompts the user with a confirm dialog. If the user clicks "OK", their password is displayed on screen.
Screenshot
Implementation
The visualization is rendered using a SVG canvas and the d3.js library. It's a bullet graph visualization, showing how long passwords have been in use, the range in which password use is healthy, and each time a password was used on a new web site.
This add-on requires data from nsiLoginManager to function. Although the code is fairly modular, Google Chrome does not offer user password data to browser extensions, so this add-on is not portable. [1]
Security Concerns
This add-on saves nothing to disk, so there is no risk of unencrypted login information leaking out to the user. The password manager will prompt the user for a master password before passing password data onto the add-on, so that security is not compromised.
However, some users seemed unaware of the way the password manager and master passwords work, and expressed concern that this add-on could give someone using their Firefox profile access to their passwords. Of course, that information is already accessible via Preferences, but it is possible that this add-on makes this information more discoverable, as many users were unaware of the Saved passwords pane in Preferences.
Password reuse data, even if unaccompanied by actual passwords or password hashes, can be of use to attackers. This add-on does not yet transmit that data in any form. Future versions may make it possible to publish screenshots of password reuse, however these screenshots contain no sensitive information.
This add-on also makes use of visual hashing, so those same security concerns apply. In particular, visual hashes are displayed for all of a user's passwords at once on the same screen, meaning screenshots of this add-on leak much more information than the previous visualization. For this reason, the password hash data in the above screenshot have been obfuscated.