Security:ThePluginProblem
Overview
Over the last many years the Mozilla Project has worked hard at trying to find and fix security bugs in the Mozilla code before attackers have been able to develop exploits. The Security Bug Bounty Program ( http://www.mozilla.org/security/bug-bounty.html ) , Frequent Security Updates we do for Firefox users ( http://www.mozilla.org/security/announce/ ) , and the aggressive updating of Firefox Users have been the cornerstones of this effort.
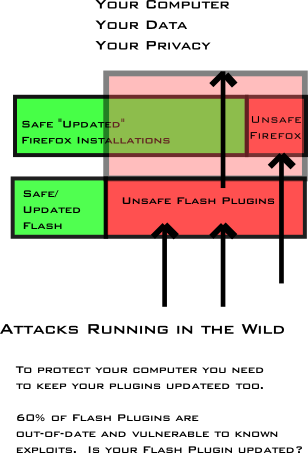
Currently it appears the greatest security risk to Firefox users is via exploitation of plugins the user has installed. A number of studies have documented this
- plugins are in wide distribution among browser users
- They are increasing a highly leveraged cross platform vector for attackers
- http://www.techzoom.net/publications/insecurity-iceberg/index.en
- (or 45.2%) Internet users at risk worldwide due to not running the latest most secure browser version. -- But Firefox actually leads the way with agressive updating of its users, while still providing choice and user control over the updates.
- Meanwhile, hidden below the surface, the iceberg extends further encompassing users that rely on outdated vulnerable browser plug-ins. Due to an inability to passively enumerate the versions of any plug-ins hosts have installed.
- http://www.trustedsource.org/blog/248/New-McAfee-Whitepaper-on-Browser-Attacks
- this study points out that most plugins only do monthly or weekly software update checks, where Firefox is doing them daily. Flash for example does its update checks monthly, which probably isn't fast enough to really keep users as safe as they should be.
- https://bugzilla.mozilla.org/show_bug.cgi?id=391433
- search for "http" to see a list of articles in this bug that talk about exploits running in the wild against plugins
- http://secunia.com/advisories/33901/2/ shows active exploit going on against Adobe Reader. minimum for 9 series should be 9.1.
- Adobe Reader 9.1 and 8.1.4 are currently under zero day so we should see and a
critical version update for those soon. http://blogs.zdnet.com/security/?p=3229
A specific example
see bug 506419 and https://bugzilla.mozilla.org/show_bug.cgi?id=391433#c83
They show Firefox users under attack from a zero day for Adobe Flash and Reader.
The common response to bugs like these is that "it's not our problem." That is true to some extent, but here are some concrete things we could do.
While we are waiting from a patch from adobe
- find new rogue .dll's in our crash reporting data and raise visibility to anti-virus companies.
- Make preparations to get firefox users to update their plugins as soon as the patch is out in 5 more days. https://bugzilla.mozilla.org/show_bug.cgi?id=391433 rather than the 5 or 6 months it might take for users to update at current rates.
- Even after the patch is out keep up the information campaign to encourage users to update. Update rates remain very slow.
Nine days after the release of a zero day fix version (July 30, 2009). http://www.adobe.com/support/security/bulletins/apsb09-10.html only around 7% of flash users have been updated.
The following shows distribution of flash versions hitting mozilla.com on Aug. 8, 2009.

Adobe is working on some fixes to this, but information campaigns will be needed until those fixes are in-place.
http://www.networkworld.com/news/2009/072709-almost-all-windows-users-vulnerable.html?ry=gs
What to do?
short term
- grass roots campaign and PR to get users' plugins upgraded - up your plugin
- maybe something that would engage the 8 million download day participants to update their plugins, and help friends and familly to update too.
- create a catalog of all high visibility pages on mozilla.com/org sumo, google start page snippets and see if we get some basic content about the issue and recommendations for users.
mid term: end of 09q3?
- make progress on morgamic's plan to build some better backend infrastructure for tracking required plugin versions, and syndicating plugin updating content. See: https://wiki.mozilla.org/Plugins:PluginCheck and https://bugzilla.mozilla.org/show_bug.cgi?id=465898
- pressure plugin vendors to upgrade users faster. Help reduce bandwidth costs for plugin vendors to do more agressive updating of their users, or help to host the updates. meeting with adobe on 8/11 to talk about his among other securty related topics.
longer term
- active plugin blocking for old versions? this strategy hasn't worked so far and many users seem to be resistant. see long discussion in : https://bugzilla.mozilla.org/show_bug.cgi?id=430826 starting around comment 72 - https://bugzilla.mozilla.org/show_bug.cgi?id=430826#c72
- fix our plugin migration code for a better upgrade experience - fx 3.6/7?
- study user experience problems and improve pop-up blocking again
- gather data from sumo and other sources to watch trends
- develop a community of malware investigators to understand more about what is happening and figure out solutions
- figure out how to help users that get into trouble
Work to help users understand plugins that are out of date, and accelerate udpates.
https://bugzilla.mozilla.org/showdependencytree.cgi?id=465898&hide_resolved=1